AWS Full CICD 2 – 为CodeBuild Service Role添加权限
根据教程1我们已经创建了CodeBuildRole, 接下来我们需要在这个role添加ECR和EKS的权限
EKS只有读取的选取,安全问题所以不能给完权限
- 去到IAM 的Roles, 然后选择刚刚创建好的Role
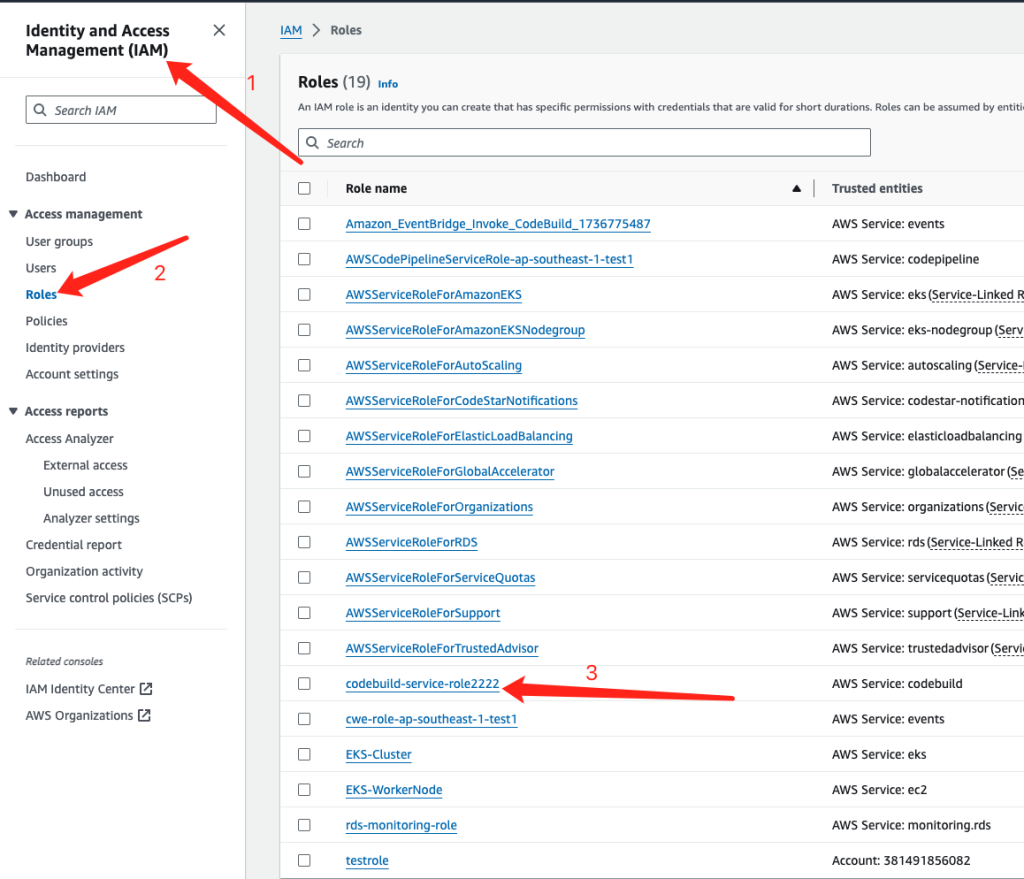
2. 选择create inline policy , 然后选择JSON格式
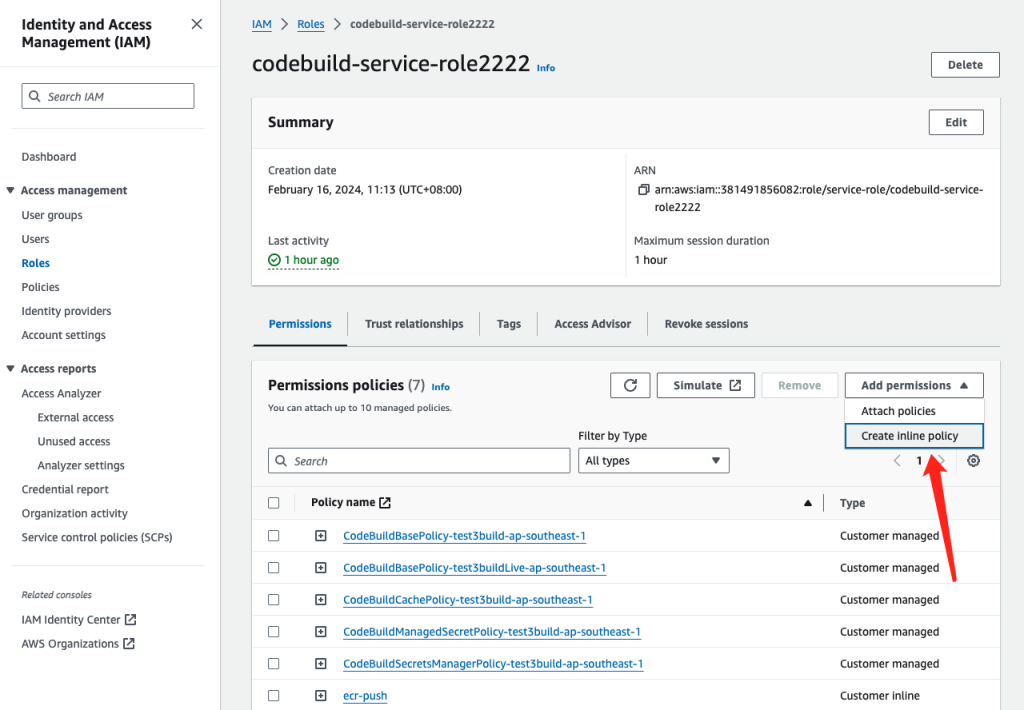
3. 添加以下两个权限
EcrPush
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Action": [
"ssm:GetParameters",
"ecr:BatchCheckLayerAvailability",
"ecr:CompleteLayerUpload",
"ecr:GetAuthorizationToken",
"ecr:InitiateLayerUpload",
"ecr:PutImage",
"ecr:UploadLayerPart",
"ecr:GetDownloadUrlForLayer",
"ecr:BatchGetImage"
],
"Resource": "*"
}
]
}EksRead
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"eks:DescribeNodegroup",
"eks:ListNodegroups",
"eks:DescribeCluster",
"eks:ListClusters",
"eks:AccessKubernetesApi",
"ssm:GetParameter",
"eks:ListUpdates",
"eks:ListFargateProfiles"
],
"Resource": "*"
}
]
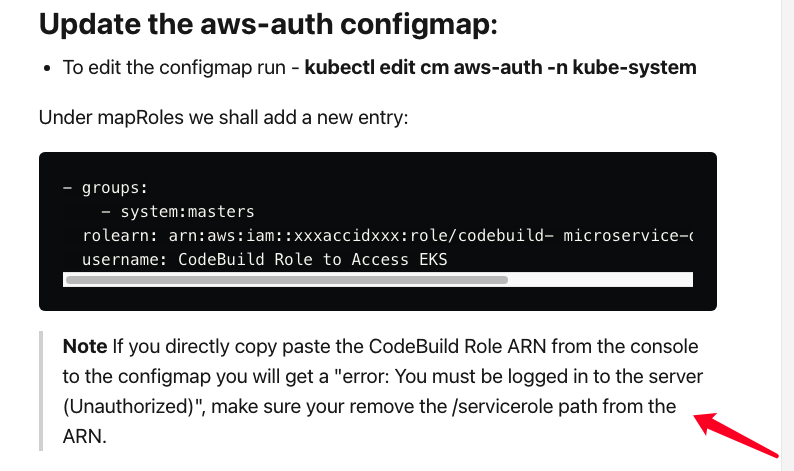
}4. 把CodeBuildRole加入到 aws-auth的ConfigMap当中,否则codebuild没有权限操作kubectl控制EKS Cluster
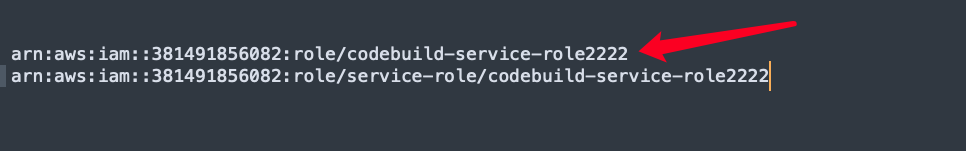
eksctl create iamidentitymapping --cluster <YourClusterName> --region <YourRegion> --arn <你的CodeBuildRole的ARN> --group system:masters --username <你的IAM CodeBuildRole名字>【注意】
系统自动创建CodeBuildServiceRole的ARN当中会有service-role, 所以必须去除,否则就会出问题
参考文章: https://dev.to/aws-builders/deploy-your-application-on-kubernetes-amazon-eks-using-aws-serverless-codebuild-594i
AWS Full CICD 1 – 创建CodeCommit Project
AWS Full CICD 2 – 为CodeBuild Service Role添加权限
AWS Full CICD 3 – 准备好buildspec.yml
![]()
Facebook评论