AWS – IAM 权限高级使用方式
参考文档: https://docs.aws.amazon.com/zh_cn/IAM/latest/UserGuide/reference_policies_condition-keys.html
- 只允许在允许IP CIDR方位内的才能访问,否则全部拒绝
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Deny",
"Action": [
"*"
],
"Resource": [
"*"
],
"Condition": {
"NotIpAddress": {
"aws:SourceIp": [
"192.0.2.0/24",
"203.0.113.0/24",
"60.48.49.94/32"
]
}
}
}
]
}2. 如果使用的region不是在ap-southeast-1和eu-west-1, 那么EC2 / RDS / DynamoDB / CodeCommit所有的功能都无法使用
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Deny",
"Action": [
"ec2:*",
"rds:*",
"dynamodb:*",
"codecommit:*"
],
"Resource": [
"*"
],
"Condition": {
"StringNotEquals": {
"aws:RequestedRegion": [
"ap-southeast-1",
"eu-west-1"
]
}
}
}
]
}3. 根据标签tagging来设权限。凡是只有EC2拥有以下2种标签的其中1种,就能start和stop instance
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["ec2:startInstances", "ec2:StopInstances"],
"Resource": "arn:aws:ec2:us-east-1:123456789012:instance/*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/Project": "DataAnalytics",
"aws:PrincipalTag/Department": "Data"
}
}
}
]
}4. 所有的EC2权限都能用,除了stop和terminate instance,要操作这2个动作的话,IAM User必须启动MFA,否则无法操作
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2:*",
"Resource": "*"
},
{
"Effect": "Deny",
"Action": ["ec2:StopInstances", "ec2:TerminateInstances"],
"Resource": "*",
"Condition": {
"BoolIfExists": {
"aws:MultiFactorAuthPresent": false
}
}
}
]
}5. 允许list出S3 Bucket当中的test bucket,允许写入,读取,删除所有test bucket底下的文件
JSON
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:ListBucket"],
"Resource": "arn:aws:s3:::test"
},
{
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:DeleteObject"
],
"Resource": "arn:aws:s3:::test/*"
}
]
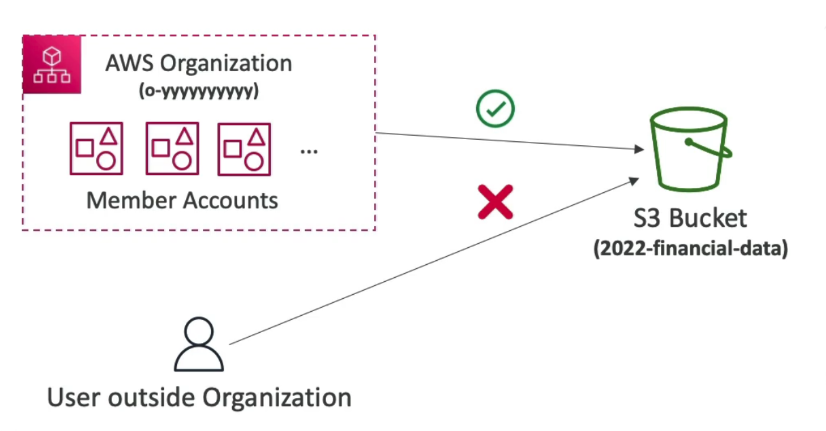
}6. 如果是under 在这个organization之下的话,那么才能够在2022-financial-data的S3 bucket底下写入或读取文件
JSON
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:PutObject", "s3:GetObject"],
"Resource": "arn:aws:s3:::2022-financial-data/*",
"Condition": {
"StringEquals": {
"aws:PrincipalOrgID": ["o-yyyyyyyyyy"]
}
}
}
]
}
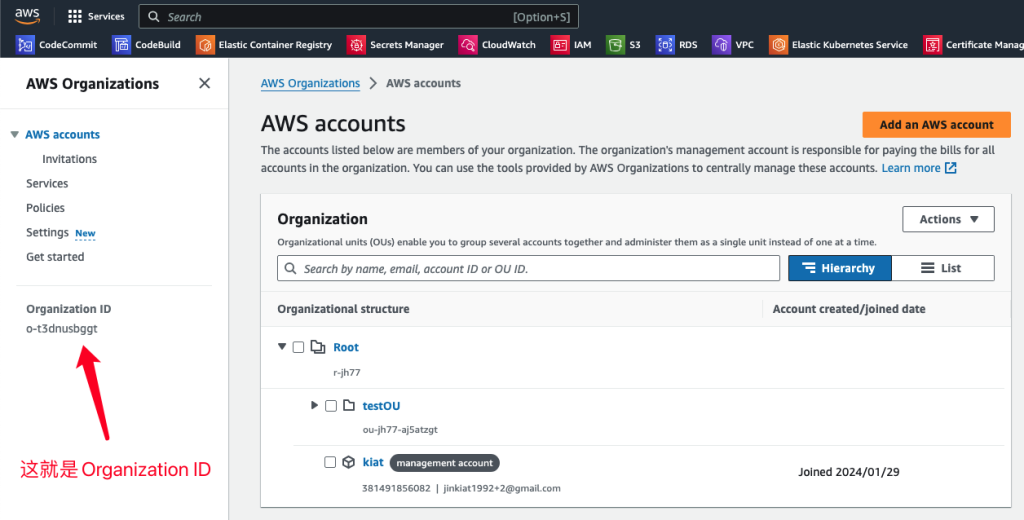
- 以下是获取Organization ID的地方
![]()
Facebook评论